When I first started managing payment systems for my clients, I remember feeling overwhelmed by the acronyms and compliance requirements. PCI DSS, PA-DSS, QSA. It seemed like alphabet soup. But here’s what I learned: understanding the PCI Data Security Standard isn’t just about checking boxes for compliance. It’s about genuinely protecting your customers’ most sensitive information.
If you’re running an e-commerce site, processing payments through your application, or managing any system that touches credit card data, this guide will walk you through everything you need to know about PCI standards.

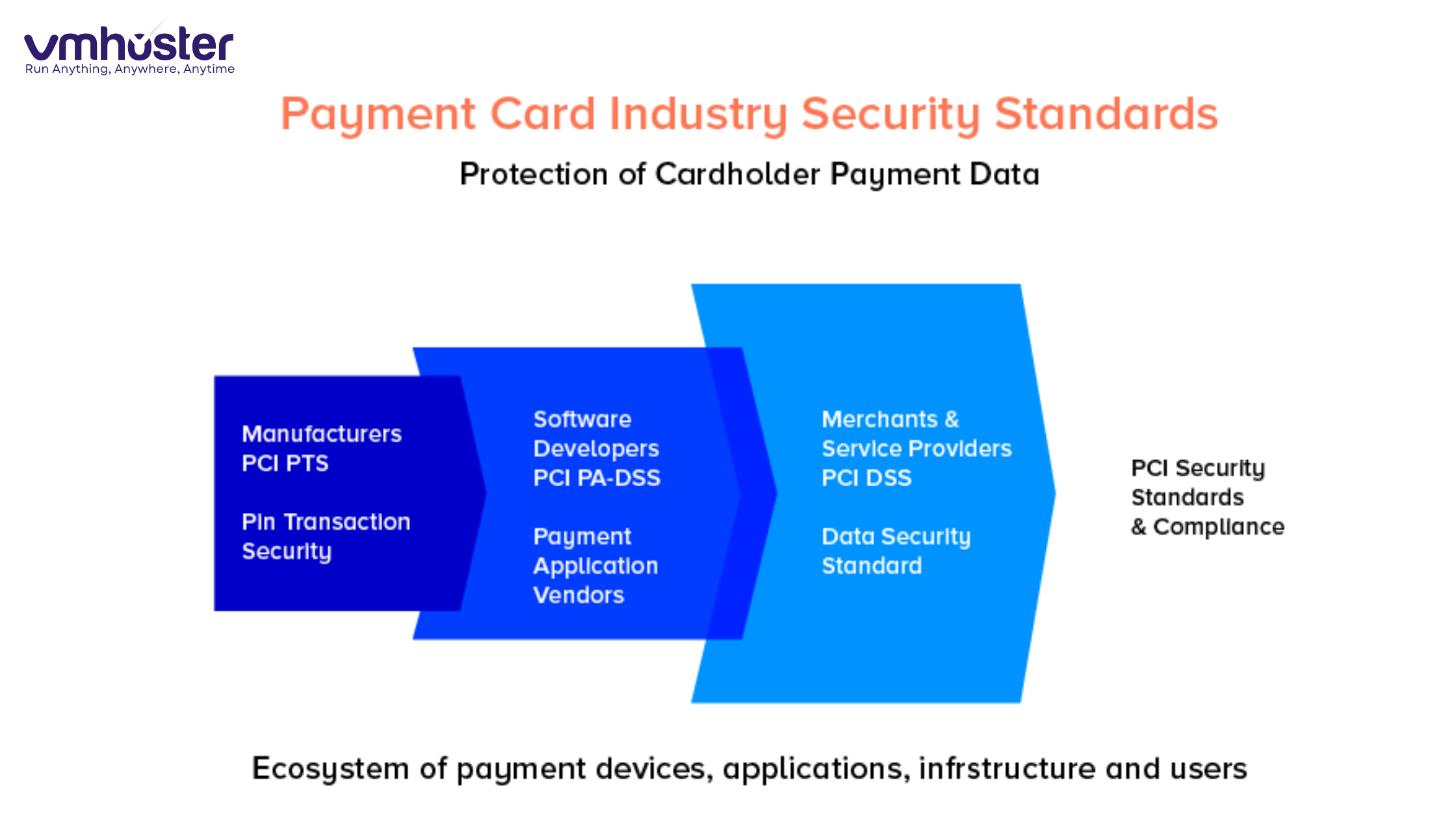
What is the PCI Data Security Standard?
The PCI Data Security Standard (PCI DSS) is a set of security requirements designed to ensure that all companies accepting, processing, storing, or transmitting credit card information maintain a secure environment. Think of it as a comprehensive security framework specifically built to protect cardholder data.
The standard was created by the Payment Card Industry Security Standards Council (PCI SSC), which was founded in 2006 by major credit card brands including Visa, Mastercard, American Express, Discover, and JCB. These companies came together because they recognized a critical need: payment data was being compromised too frequently, and there needed to be a unified approach to security.
Here’s something most people don’t realize. PCI DSS isn’t technically a law. It’s a contractual obligation. When you agree to accept credit cards from these major brands, you’re contractually required to comply with their security standards. However, some states have incorporated PCI compliance into their data breach laws, making it legally relevant as well.
What Are PCI Standards? Breaking Down the Requirements
When people ask “what are PCI standards,” they’re usually referring to the 12 core requirements organized into six control objectives. I’ve found that understanding these objectives makes the whole framework much more approachable.
The Six Control Objectives
1. Build and Maintain a Secure Network
This is your foundation. It includes:
- Installing and maintaining firewall configurations to protect cardholder data
- Never using vendor-supplied defaults for system passwords and security parameters
I learned this lesson the hard way when a client’s system was breached because they’d left default admin credentials unchanged. It’s Security 101, but you’d be surprised how often it’s overlooked.
2. Protect Cardholder Data
This objective focuses on:
- Protecting stored cardholder data through encryption
- Encrypting transmission of cardholder data across public networks
Here’s a real-world example: If you’re storing credit card numbers in your database, they must be encrypted using strong cryptography. Even if someone gains unauthorized access to your database, the data should be unreadable without the encryption keys.
3. Maintain a Vulnerability Management Program
This includes:
- Using and regularly updating anti-virus software
- Developing and maintaining secure systems and applications
Think of this as your ongoing health checkup for your systems. Just like you wouldn’t skip annual medical exams, you can’t skip security patches and vulnerability assessments.
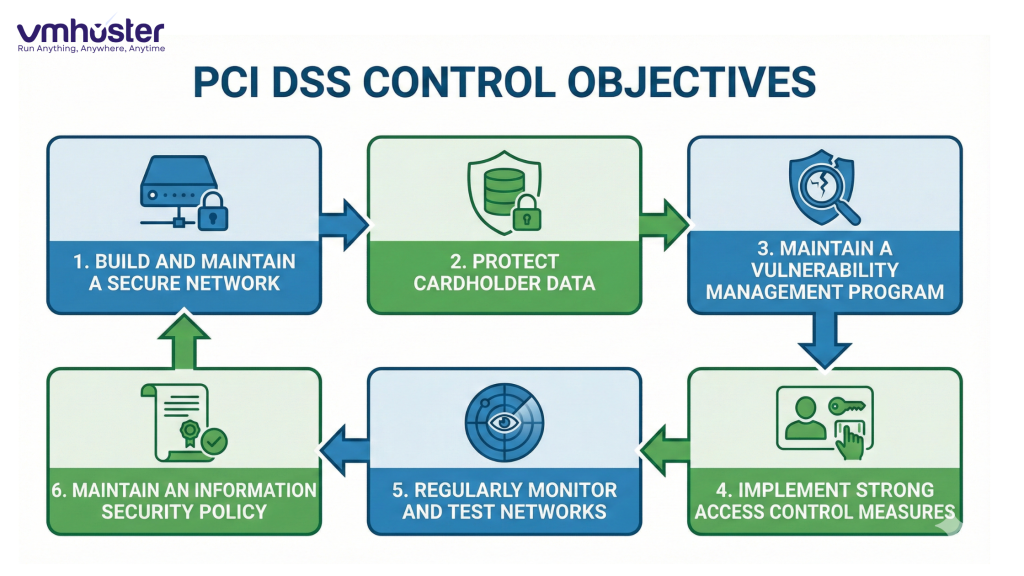
4. Implement Strong Access Control Measures
Access control requirements include:
- Restricting access to cardholder data by business need-to-know
- Assigning unique IDs to each person with computer access
- Restricting physical access to cardholder data
I always tell my clients: treat cardholder data like your most valuable possession. Not everyone in your organization needs access to it—only those whose job absolutely requires it.
5. Regularly Monitor and Test Networks
This involves:
- Tracking and monitoring all access to network resources and cardholder data
- Regularly testing security systems and processes
Logging is crucial here. If something goes wrong, you need to be able to trace what happened, when, and by whom.
6. Maintain an Information Security Policy
Finally, you need:
- A comprehensive security policy that addresses information security for employees and contractors
This isn’t just a document that sits in a drawer. Your PCI security policy should be a living document that guides how everyone in your organization handles payment data.
Understanding PCI Security Policy Requirements
Let me share something from my experience: many businesses fail PCI audits not because of technical shortcomings, but because their security policies are inadequate or poorly documented.
What Makes a Strong PCI Security Policy?
Your PCI security policy needs to address several critical areas:
Risk Assessment Procedures You should conduct annual risk assessments to identify threats to cardholder data. I recommend documenting not just the risks you find, but also the mitigation strategies you implement.
Acceptable Use Policies Define clearly how employees can use company technology, especially systems that handle payment data. For instance, should employees be allowed to use personal USB drives on systems processing cardholder data? (Spoiler: probably not.)
Incident Response Plan When—not if—a security incident occurs, your team needs to know exactly what to do. Your incident response plan should include:
- Who to contact immediately
- How to contain the breach
- Evidence preservation procedures
- Communication protocols
Employee Training Requirements Everyone who handles cardholder data needs regular security awareness training. I’ve seen this make a real difference—educated employees are your first line of defense against social engineering and phishing attacks.
PCI DSS Compliance Levels: Where Do You Fit?
Not all businesses face the same PCI requirements. The compliance level depends on your transaction volume:
Level 1: Merchants processing over 6 million transactions annually
Level 2: Merchants processing 1-6 million transactions annually
Level 3: Merchants processing 20,000-1 million e-commerce transactions annually
Level 4: Merchants processing fewer than 20,000 e-commerce transactions or up to 1 million total transactions annually
Here’s what this means practically: If you’re a Level 1 merchant, you’ll need an annual on-site audit by a Qualified Security Assessor (QSA). Smaller merchants can often complete a Self-Assessment Questionnaire (SAQ), though requirements vary by card brand and acquiring bank.
For most small to medium businesses I work with, reducing your PCI scope is a smart strategy. If you’re using a reputable payment processor like Stripe, Square, or PayPal, and implementing their hosted payment forms, you might only need to complete SAQ-A, the simplest questionnaire. Check out VMHoster’s secure hosting solutions which can help reduce your PCI compliance scope.
Common PCI Compliance Challenges (And How to Overcome Them)
In my years helping businesses achieve PCI compliance, I’ve noticed the same challenges come up repeatedly:
Challenge 1: Scope Creep
The problem: Cardholder data spreads across your systems like digital kudzu. It ends up in logs, backup files, email attachments, and development databases.
The solution: Implement strict data retention policies and regularly scan your systems for cardholder data in unexpected places. Use data discovery tools to find where payment information might be hiding.
Challenge 2: Vendor Management
The problem: You’re responsible for your vendors’ security practices if they handle your cardholder data.
The solution: Maintain a detailed inventory of all third-party service providers who access your cardholder data environment. Ensure they’re PCI compliant and get annual attestations of compliance (AOCs) from them.
Challenge 3: Documentation Fatigue
The problem: PCI requires extensive documentation—policies, procedures, network diagrams, evidence of testing, training records, and more.
The solution: Don’t wait until audit time. Make documentation an ongoing process. I use a compliance calendar to track when each piece of documentation needs updating.
PCI DSS Version 4.0: What’s Changed?
The PCI Security Standards Council released PCI DSS version 4.0 in March 2022, with businesses having until March 2025 to fully transition from version 3.2.1. If you haven’t started preparing, now’s the time.
Key changes include:
Customized Implementation Version 4.0 introduces more flexibility with “Customized Approach” options alongside the traditional “Defined Approach.” This allows organizations to implement security controls differently as long as they meet the objective.
Enhanced Authentication Requirements Multi-factor authentication (MFA) requirements have been expanded. Where version 3.2.1 required MFA for remote access to the cardholder data environment, version 4.0 extends this to all access to the CDE.
Better Risk Management There’s now a requirement to implement targeted risk analyses as part of security control selection and implementation.
For detailed guidance on the transition, the PCI Security Standards Council’s official documentation at https://www.pcisecuritystandards.org is invaluable.
Practical Steps to Achieve PCI Compliance
Let me walk you through the process I use with clients:
Step 1: Determine Your Compliance Level
Calculate your annual transaction volume and determine which SAQ applies to your situation. Your acquiring bank can help with this.
Step 2: Complete a Compliance Audit
Even before your official assessment, conduct an internal audit. Use the appropriate SAQ as a checklist and identify gaps.
Step 3: Remediate Vulnerabilities
Address the gaps you’ve identified. Prioritize based on risk—some vulnerabilities pose immediate threats while others are lower priority.
Step 4: Complete Your SAQ
If you’re not required to use a QSA, complete the appropriate Self-Assessment Questionnaire honestly and thoroughly.
Step 5: Scan Your Network
Conduct quarterly vulnerability scans using an Approved Scanning Vendor (ASV). These scans are required for most compliance levels.
Step 6: Submit Documentation
Provide your SAQ, Attestation of Compliance (AOC), and scan reports to your acquiring bank and card brands as required.
Step 7: Maintain Compliance
This isn’t a one-and-done process. PCI compliance is ongoing. Implement quarterly scans, annual assessments, and continuous monitoring.
The Business Case for PCI Compliance
I know compliance can seem like a burden—another checkbox, another cost. But consider this: according to IBM’s Cost of a Data Breach Report, the average cost of a data breach in 2024 was $4.45 million. For small businesses, a single breach can be existential.
Beyond avoiding breaches, PCI compliance offers real benefits:
Customer Trust: Displaying security badges and certifications can increase conversion rates. Customers want to know their payment data is safe.
Reduced Liability: While PCI compliance doesn’t eliminate liability in case of a breach, it can significantly reduce penalties and demonstrates due diligence.
Operational Excellence: The security practices required by PCI DSS generally improve your overall security posture, protecting not just payment data but all your sensitive information.
Choosing the Right Hosting for PCI Compliance
Your hosting infrastructure plays a crucial role in PCI compliance. If you’re using shared hosting where multiple websites share the same server, your PCI compliance becomes much more complicated and potentially impossible.
What to look for in PCI-compliant hosting:
- Network Segmentation: Your cardholder data environment should be isolated from other systems
- Regular Security Updates: Automatic patching and updates
- Firewall Protection: Both hardware and software firewalls properly configured
- Intrusion Detection: Systems to monitor and alert on suspicious activity
- Physical Security: Data center access controls and monitoring
If you’re handling payment data directly, consider working with hosting providers who understand PCI requirements. At VMHoster, we provide infrastructure designed with security compliance in mind, helping reduce the complexity of achieving and maintaining PCI certification.
Resources for Staying PCI Compliant
Here are resources I regularly reference:
Official Documentation:
- PCI Security Standards Council: https://www.pcisecuritystandards.org
- PCI DSS Quick Reference Guide (regularly updated)
Tools and Services:
- NIST Cybersecurity Framework: https://www.nist.gov/cyberframework
- SANS Institute Security Resources: https://www.sans.org
Training: Consider becoming a PCI Internal Security Assessor (ISA) if you’re responsible for compliance at a larger organization. The PCI SSC offers training programs.
Common Myths About PCI Compliance
Let me clear up some misconceptions I hear frequently:
Myth 1: “We use a third-party processor, so we don’t need to be PCI compliant.” Reality: You still have compliance obligations, though your scope may be reduced. You’re responsible for how you integrate with that processor.
Myth 2: “We’re too small to be audited.” Reality: While you may not need a formal audit, you’re still contractually obligated to comply. Plus, card brands can fine acquiring banks for non-compliant merchants, and those costs get passed to you.
Myth 3: “Once we’re compliant, we’re done.” Reality: PCI compliance is continuous. Requirements include quarterly scans, regular testing, and annual assessments.
Final Thoughts: Making PCI Compliance Work for You
Looking back at my journey with PCI compliance, I realize it’s taught me more than just security checklists. It’s taught me to think systematically about protecting sensitive data, to document thoroughly, and to always assume that attackers are probing for weaknesses.
Yes, PCI compliance requires effort and investment. But it’s not just about avoiding fines—it’s about building a security-conscious culture that protects your customers, your reputation, and ultimately your business.
Start small if you need to. Pick one requirement and implement it properly. Then move to the next. Before you know it, you’ll have built a robust security program that not only meets PCI requirements but genuinely protects your business.
If you’re feeling overwhelmed, remember: you don’t have to do this alone. Work with qualified security assessors, leverage compliant hosting providers, and don’t hesitate to seek expert advice. The investment you make today in proper security practices will pay dividends for years to come.