I still remember the first time a client’s website went down because their SSL certificate expired. It was 2 AM, and I was frantically trying to figure out what went wrong. That’s when I discovered OpenSSL’s command-line tools, and honestly, they’ve saved me countless times since then.
If you’re managing web servers, working with HTTPS, or just trying to troubleshoot SSL issues, knowing how to check SSL certificates with OpenSSL is an essential skill. Today, I’ll walk you through everything you need to know about testing and verifying SSL certificates using OpenSSL.
What is OpenSSL and Why Use It?
OpenSSL is a robust, open-source toolkit that implements SSL (Secure Sockets Layer) and TLS (Transport Layer Security) protocols. It’s basically the Swiss Army knife for anything related to SSL certificates and encryption.
Most Linux distributions come with OpenSSL pre-installed, which makes it incredibly convenient. Unlike web-based SSL checkers, OpenSSL gives you direct access to certificate details, works offline, and doesn’t require sharing your server information with third parties.
Quick Check: Testing SSL Certificate on a Live Website
Let’s start with the most common scenario – checking the SSL certificate of a live website. This is what I use almost daily when clients ask me to verify their SSL setup.
Basic SSL Certificate Check
Open your terminal and run this command:
openssl s_client -connect example.com:443 -servername example.com
Replace example.com with your actual domain. The -servername flag is crucial for servers hosting multiple SSL certificates (SNI – Server Name Indication).
You’ll see a massive output, but don’t worry. The important parts include:
- Certificate chain
- Server certificate details
- SSL/TLS protocol version
- Cipher suite information
Getting Just the Certificate Information
If you want cleaner output without all the connection details, pipe the command like this:
echo | openssl s_client -connect example.com:443 -servername example.com 2>/dev/null | openssl x509 -noout -text
This gives you a formatted, readable certificate with all the juicy details.
How to Check SSL Certificate Expiration Date
Certificate expiration is probably the #1 reason websites suddenly show SSL errors. I’ve learned to set reminders 30 days before expiration because trust me, you don’t want angry emails from users seeing “Your connection is not private” warnings.
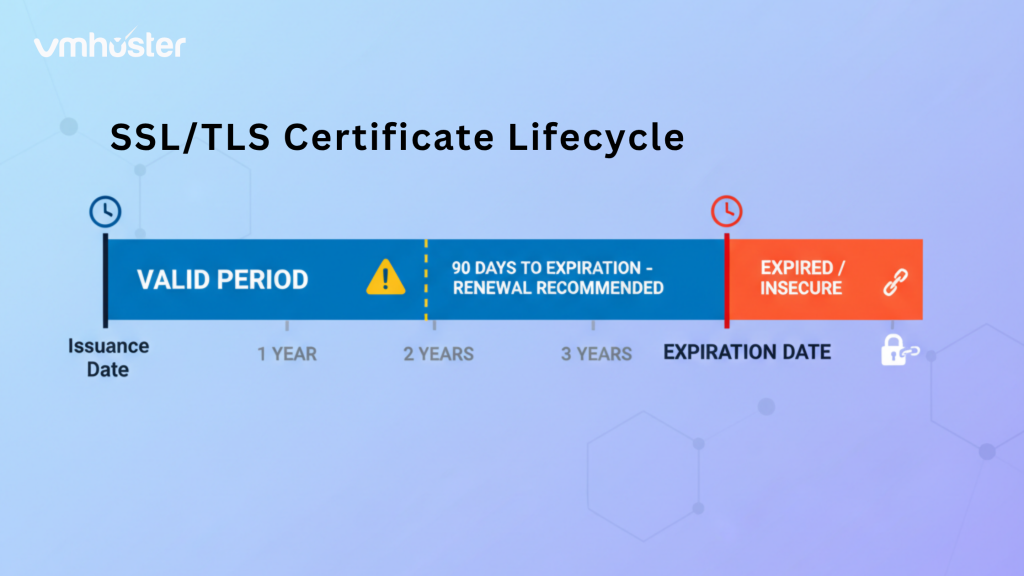
Use this command to check expiration dates:
echo | openssl s_client -connect example.com:443 -servername example.com 2>/dev/null | openssl x509 -noout -dates
You’ll see output like:
notBefore=Jan 15 00:00:00 2025 GMT
notAfter=Apr 15 23:59:59 2025 GMT
Want to know exactly how many days are left? Try this:
echo | openssl s_client -connect example.com:443 -servername example.com 2>/dev/null | openssl x509 -noout -enddate | cut -d= -f2 | xargs -I {} date -d {} +%s | awk '{print int(($1 - systime()) / 86400)}'
Checking Local SSL Certificate Files
Sometimes you need to inspect a certificate file before installing it on your server. Maybe you just generated a new certificate, or you’re migrating from another server.
View Certificate Details from a File
openssl x509 -in certificate.crt -text -noout
This works with .crt, .pem, or .cer files. You’ll see:
- Issuer information
- Subject (your domain)
- Validity period
- Public key details
- Signature algorithm
Verify Certificate and Private Key Match
Here’s something that bit me early in my career: deploying mismatched certificate and key files. The server starts, but SSL doesn’t work. Use these commands to verify they match:
openssl x509 -noout -modulus -in certificate.crt | openssl md5
openssl rsa -noout -modulus -in private.key | openssl md5
If the MD5 hashes match, you’re good to go. If they don’t, you’ve got the wrong pair.
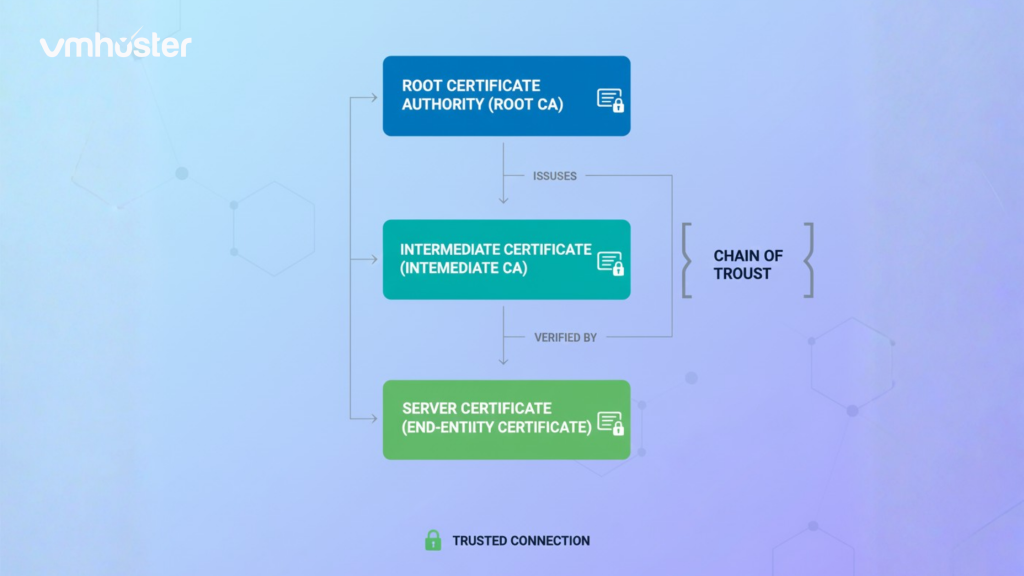
Checking SSL Certificate Chain
Certificate chains can be tricky. Your certificate needs to link back to a trusted root certificate authority (CA) through intermediate certificates.
openssl s_client -connect example.com:443 -showcerts
This displays the entire certificate chain. Look for “Verify return code: 0 (ok)” at the bottom – that’s what you want to see.
Testing Specific SSL/TLS Versions
With older SSL versions being deprecated due to security vulnerabilities, sometimes you need to test which protocols a server supports.
For TLS 1.2:
openssl s_client -connect example.com:443 -tls1_2
For TLS 1.3:
openssl s_client -connect example.com:443 -tls1_3
If the connection succeeds, that protocol version is supported. If it fails, it’s either disabled or not supported.
Common SSL Certificate Issues and How to Diagnose Them
Over the years, I’ve encountered pretty much every SSL error imaginable. Here are the most common ones:
Self-Signed Certificate Error
- Issue: “self signed certificate” error
- Solution: Add
-CAfileflag pointing to your CA bundle, or use-verify_return_errorto see detailed errors
Hostname Mismatch
- Issue: Certificate issued for different domain
- Check with:
openssl x509 -in certificate.crt -noout -subject -ext subjectAltName
Expired Certificate
- Most obvious but catches everyone eventually
- Automate checks using cron jobs with the expiration command above

Checking Certificate from a Specific Port
Not all SSL services run on port 443. Email servers, for instance, use different ports:
openssl s_client -connect mail.example.com:465 -servername mail.example.com
Common ports:
- 443: HTTPS
- 465: SMTPS
- 587: SMTP with STARTTLS
- 993: IMAPS
- 995: POP3S
Pro Tips for SSL Certificate Management
After working with SSL certificates for years, here are some lessons I’ve learned the hard way:
- Always keep backups of your private keys in a secure location
- Set up monitoring – use tools like Nagios or simple cron jobs to alert you 30 days before expiration
- Document your certificates – maintain a spreadsheet with domains, expiration dates, and issuer information
- Use Let’s Encrypt when possible – free, automated, and renews every 90 days (check out our guide on setting up Let’s Encrypt on your VPS)
- Test after deployment – always verify your SSL setup after installing or renewing certificates
Automating SSL Certificate Checks
For production environments, manual checks aren’t scalable. Here’s a simple bash script I use:
#!/bin/bash
DOMAIN="example.com"
EXPIRY_DATE=$(echo | openssl s_client -connect $DOMAIN:443 -servername $DOMAIN 2>/dev/null | openssl x509 -noout -enddate | cut -d= -f2)
EXPIRY_EPOCH=$(date -d "$EXPIRY_DATE" +%s)
CURRENT_EPOCH=$(date +%s)
DAYS_LEFT=$(( ($EXPIRY_EPOCH - $CURRENT_EPOCH) / 86400 ))
if [ $DAYS_LEFT -lt 30 ]; then
echo "WARNING: SSL certificate for $DOMAIN expires in $DAYS_LEFT days!"
fi
You can enhance this and in`tegrate it with your monitoring system or email alerts.
Wrapping Up
Learning to check SSL certificates with OpenSSL might seem intimidating at first, but once you get comfortable with these commands, you’ll wonder how you ever managed without them. Whether you’re troubleshooting SSL issues, verifying certificate installations, or just doing routine security checks, OpenSSL gives you the transparency and control you need.
The best part? Everything happens in your terminal, so you can script, automate, and integrate these checks into your existing workflows. If you’re running a VPS or dedicated server with VMhoster, having these skills in your toolkit will make SSL management infinitely easier.
Got questions about SSL certificates or OpenSSL commands? Drop them in the comments below – I read and respond to every one!
Related Resources:
Keywords: how to check ssl certificate with openssl, checking ssl certificate with openssl, test certificate openssl, check ssl certificate with openssl, openssl commands, ssl verification, certificate expiration check.